In the modern digital age, your computer is susceptible to a variety of malicious software, also known as malware. Whether you’re an ordinary user or a company professional, understanding how malware infects your computer is critical for protecting your data and privacy. Malware can take many forms, which include phishing emails to malicious downloads, and each poses its own set of risks. In this article, we will look at the most common ways malware can infiltrate your computer and provide advice on how to stay safe from these cyber threats.
1. Malicious Office macros
Microsoft Office includes a powerful scripting language that enables developers to create advanced tools to help you work more efficiently. However, criminals can use that scripting language to write malicious scripts that install malware or perform other unwanted behaviors.
If you open an Office file and see a message like this:
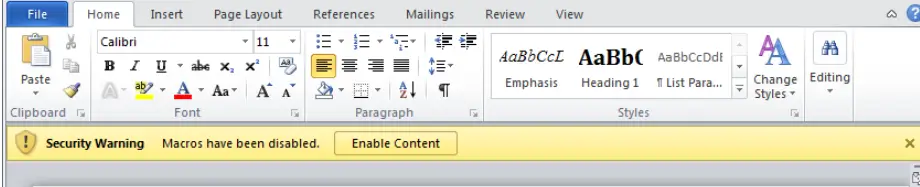
Do NOT enable that content unless you are certain you understand what it does, even if the file appears to be from someone you trust.
2. Infected removable drives
Many bugs spread by infecting removable devices like USB flash drives or external hard drives. When you connect an infected drive to your PC, the malware may be automatically installed.
To avoid this type of infection, you can do the following:
First of all, be very careful of any USB device that you do not own. If you come across a USB device that appears to have been lost or discarded, be wary of plugging it into a computer that contains sensitive information. Sometimes attackers purposefully leave infected USB devices in public places in the hopes that someone will find them and plug them into their computer. This is known as USB drop attack. If you plug an unknown removable device into your computer, run a security scan immediately.
3. Bundled with other software
Some malware can be installed along with other downloaded programs. This includes software from third-party websites as well as files shared via peer-to-peer networks.
Some programs will also install other software that Microsoft marks as potentially unwanted. This can include toolbars or programs that display additional advertisements as you browse the web. Typically, you can opt out of installing this extra software by checking a box during the installation process. Windows Security can help keep you safe from potentially harmful applications.
Malware is frequently installed alongside software key generators. Microsoft security software detects malware on more than half of PCs that have keygens installed.
To avoid installing malware or potentially unwanted software, as follows:
- Always download from the vendor’s official website.
- Read installation instructions carefully before clicking OK.
4. Hacked or compromised webpages
Malware can infect your PC by exploiting known software .
When you visit a website, it may attempt to infect your computer with malware by exploiting web browser permeability. The website could be malicious, or it could be legitimate but hacked or compromised.
This is why it is critical to keep all of your software, particularly your web browser, up to date and to remove any software that you no longer use. This includes any unused browser extensions.
You can reduce your chances of getting malware in this way by using a modern browser, such as Microsoft Edge, and keeping it up to date.
Read Also: What is a Shortcut Virus and how to remove it?
5. Spam emails
Malware writers frequently attempt to trick you into downloading malicious files. This could be an email with a file attached that contains a delivery receipt, a tax refund, or an invoice for a ticket. It may state that you must open the attachment in order to receive the items or money.
If you open the attachment, you will end up installing malware on your computer.
A malicious email can sometimes be easily identified—it may have poor spelling and grammar or come from an email address you have never seen before. These emails, however, can appear to be from a legitimate business or a person you know. Malware can hack email accounts and send malicious spam to contacts it finds.
To reduce the chances of your device becoming infected:
- Do not open emails from unknown senders or if they do not appear to be legitimate.
- Avoid clicking unexpected links in emails.
- Even if an email appears to be from someone you can trust, never open unexpected attachments.
6. Other malware
Some malware can download additional threats to your computer. Once these threats are installed on your PC, they will continue to download new threats.
The best protection against malware and potentially unwanted software is to use an up-to-date, real-time security product like Microsoft Defender Antivirus, Malware Bytes, Malicious Software Removal Tool, etc.
Read Also: Block USB Storage Devices Without Affecting Keyboard, Mouse, and Printer
Conclusion
It is more important than ever to protect your computer against malware. You can significantly reduce your risk of infection by staying informed about how malware spreads and implementing security best practices such as using reputable antivirus software, avoiding suspicious links, and keeping your system up to date. Remember that cybercriminals are constantly changing their strategies, so staying vigilant is essential. Adopt strong cybersecurity habits and scan your computer for malware on a regular basis to keep your data safe.